Flare-on 4
Challenge #1: Login.html
First we open the file and we can see the page
Directly looked at the web source code
1 |
|
We found a very important sentence: PyvragFvqrYbtvafNerRnfl@syner-ba.pbz" == rotFlag and You can see it’s a rot13
We use python :
1 | print "PyvragFvqrYbtvafNerRnfl@syner-ba.pbz".decode('rot13') //ClientSideLoginsAreEasy@flare-on.com |
Challenge #2: IgniteMe
Open the file
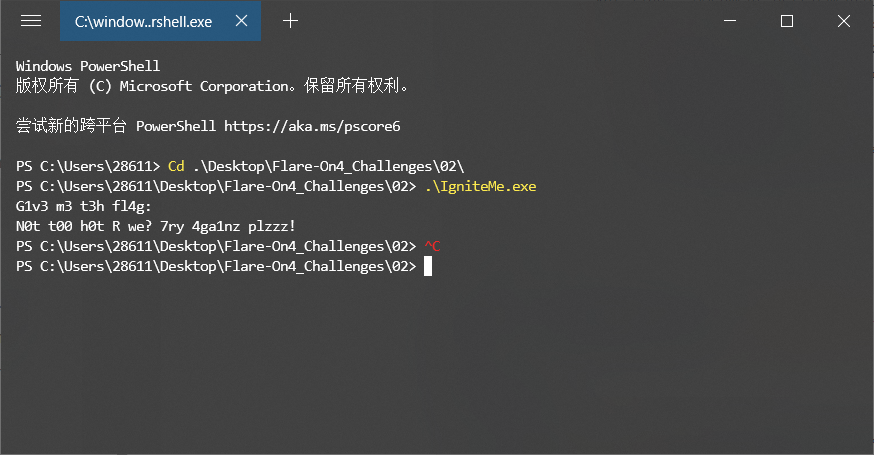
Put it in IDA for analysis
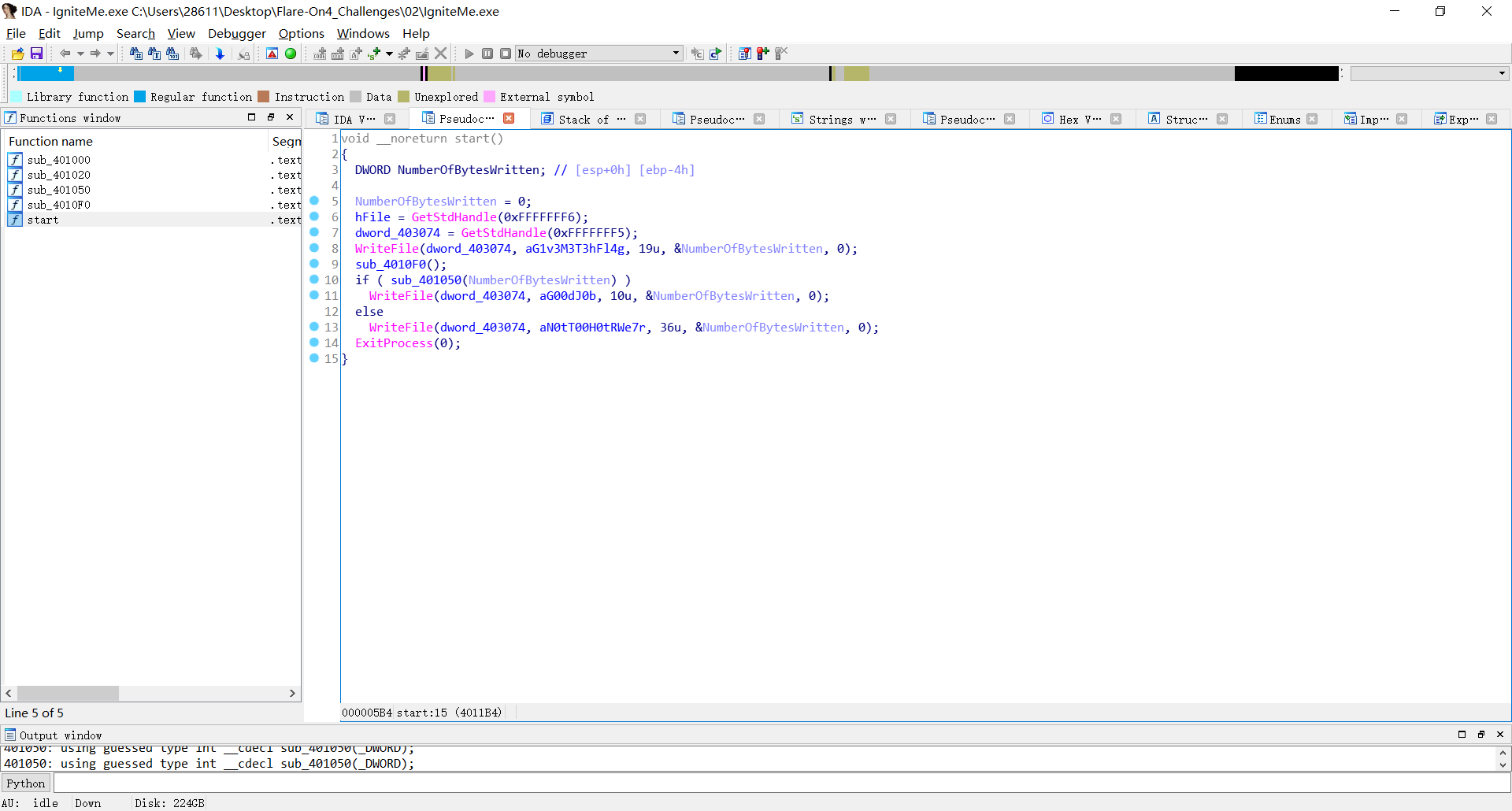
We need to know about WriteFile
1 | BOOL WriteFile ( |
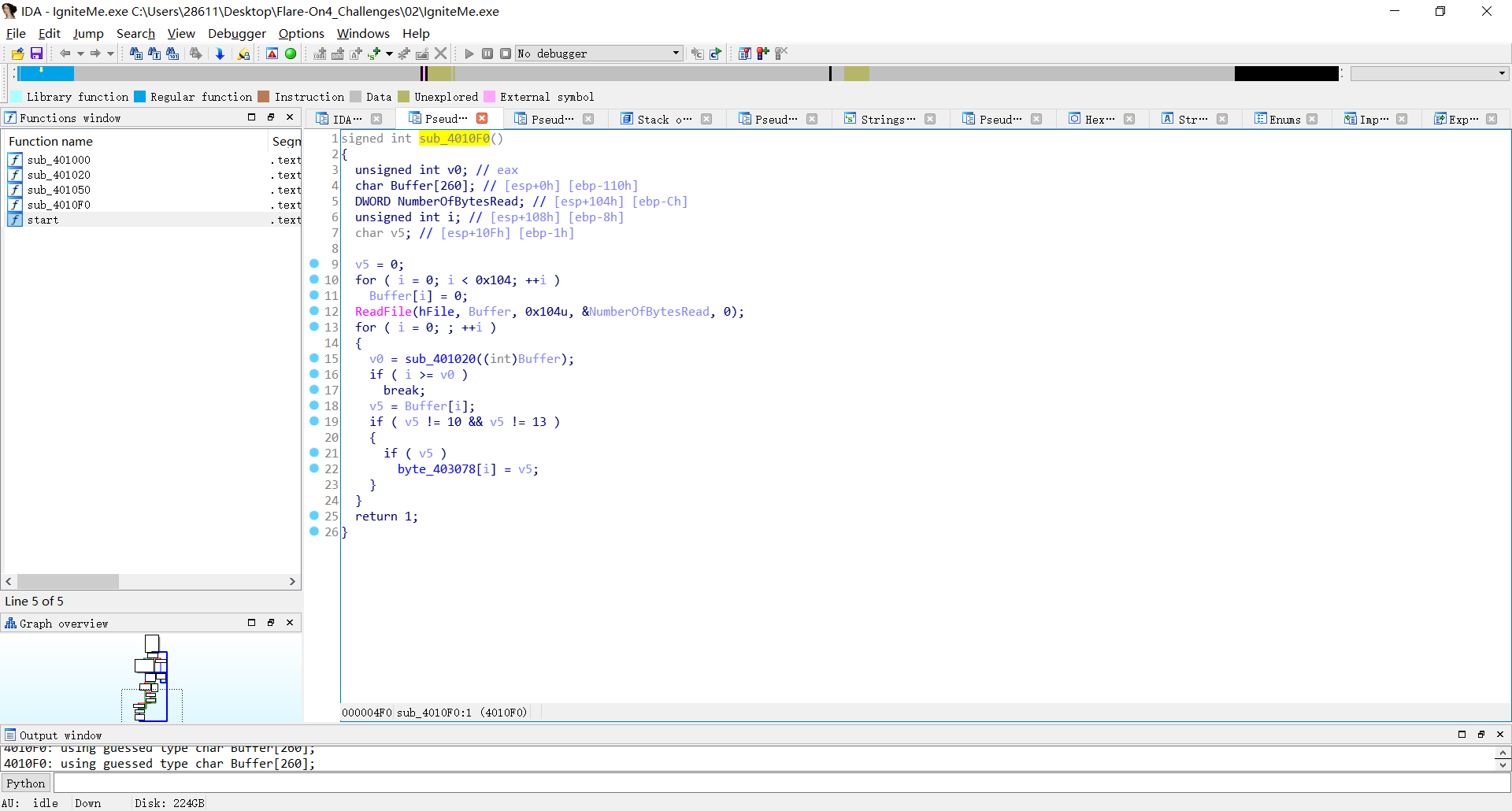
sub_4010F0 function is used to read and store user input data 0x403078, we can find sub_401050.This function this decision function
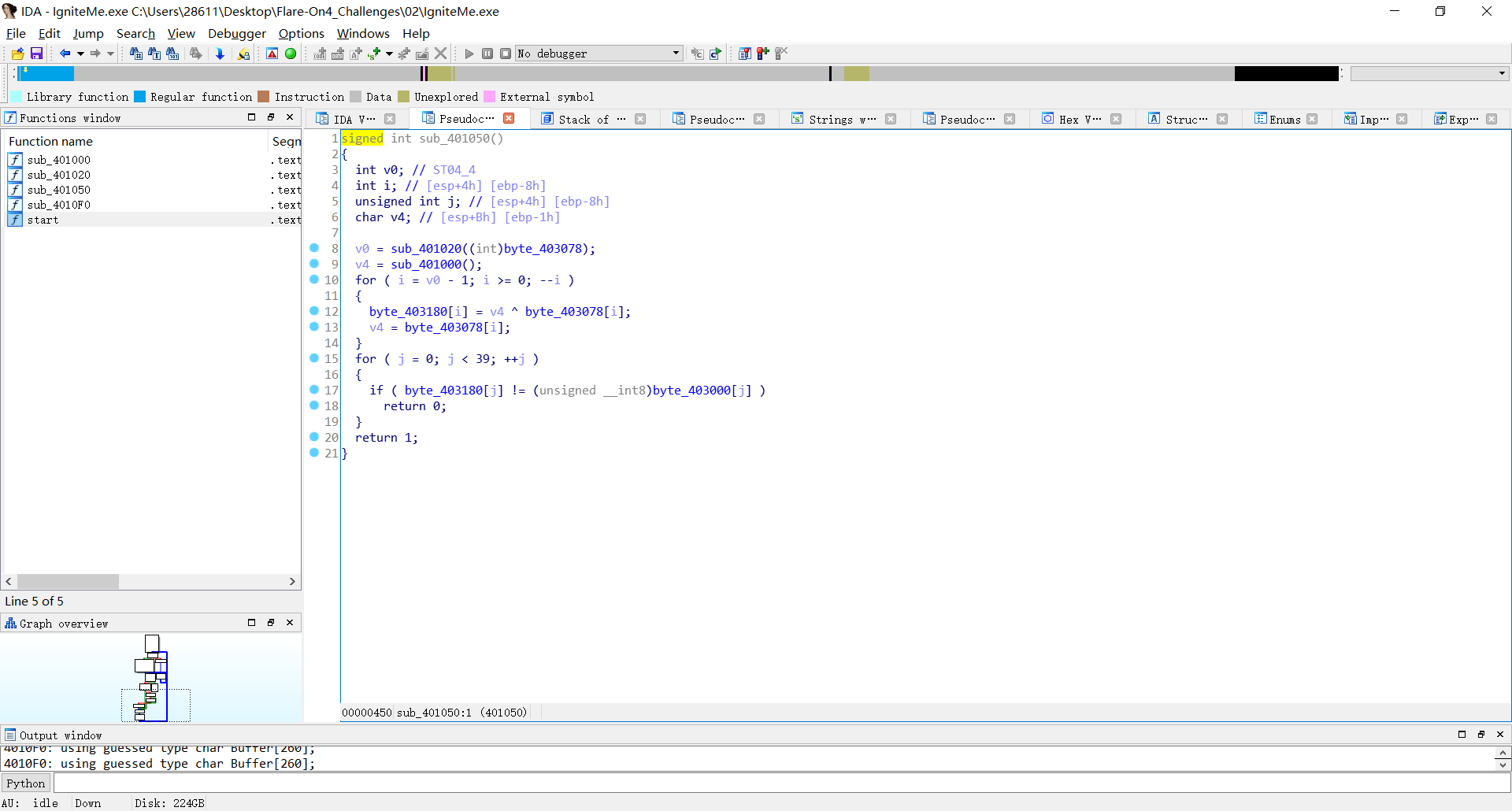
We find v4 = (unsigned __int16)ROL4(-2147024896, 4) >> 1 in sub_401000
1 | sub_401000 proc near ; CODE XREF: sub_401050+16↓p |
The loop moves 4 bits to the left and 1 bit to the right,we have v4 starting at 4(int16 = 16Bits)
1 | cipher = [0x0D, 0x26, 0x49, 0x45, 0x2A, 0x17, 0x78, 0x44, 0x2B, 0x6C, 0x5D, 0x5E, 0x45, 0x12, 0x2F, 0x17, 0x2B, 0x44, 0x6F, 0x6E, 0x56, 0x09, 0x5F, 0x45, 0x47, 0x73, 0x26, 0x0A, 0x0D, 0x13, 0x17, 0x48, 0x42, 0x01, 0x40, 0x4D, 0x0C, 0x02, 0x69] |
Challenge #3: greek_to_me
Open the file
I don’t know what’s going on here, there’s no response, there’s no input, i put it into ida
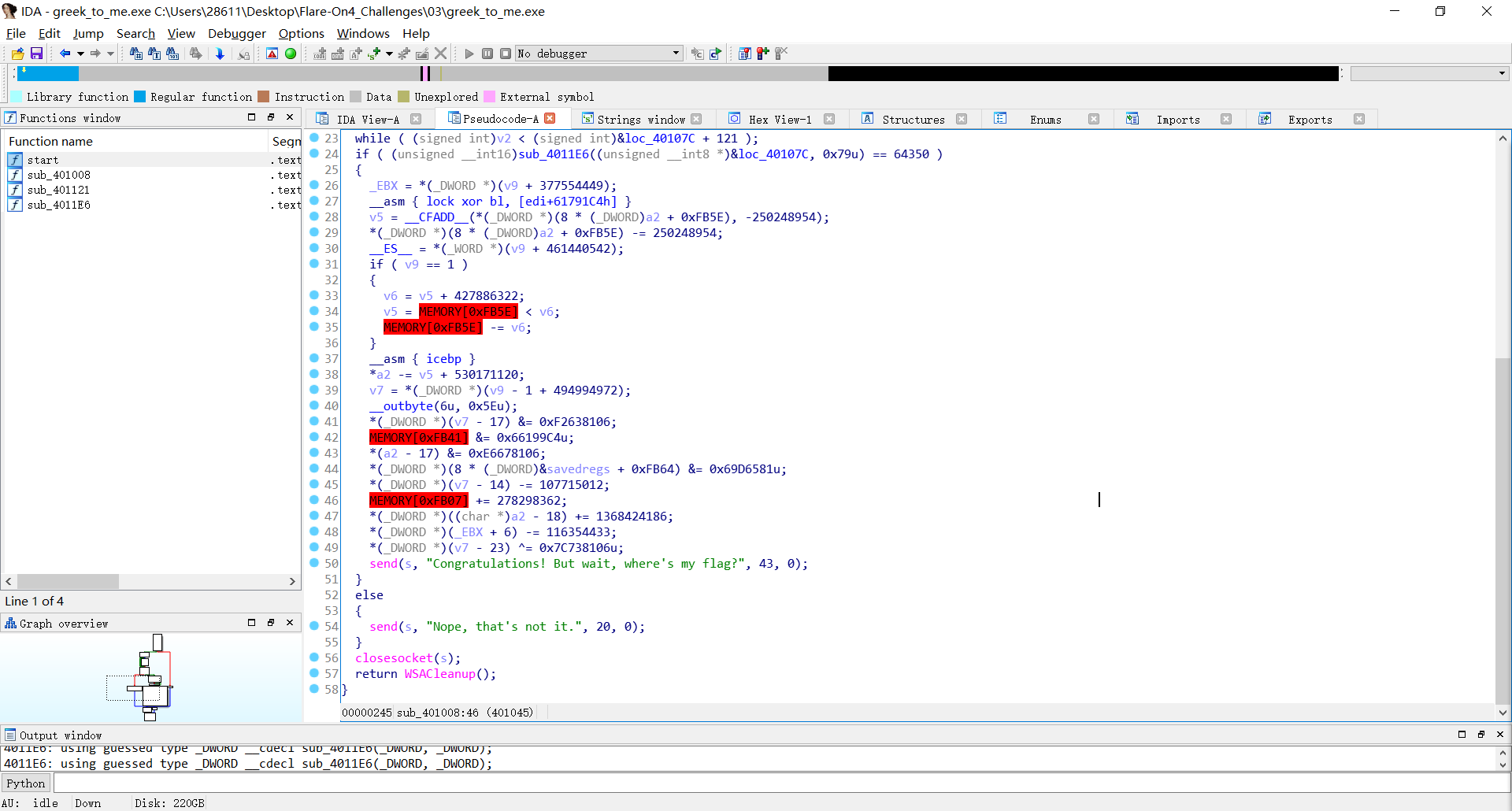
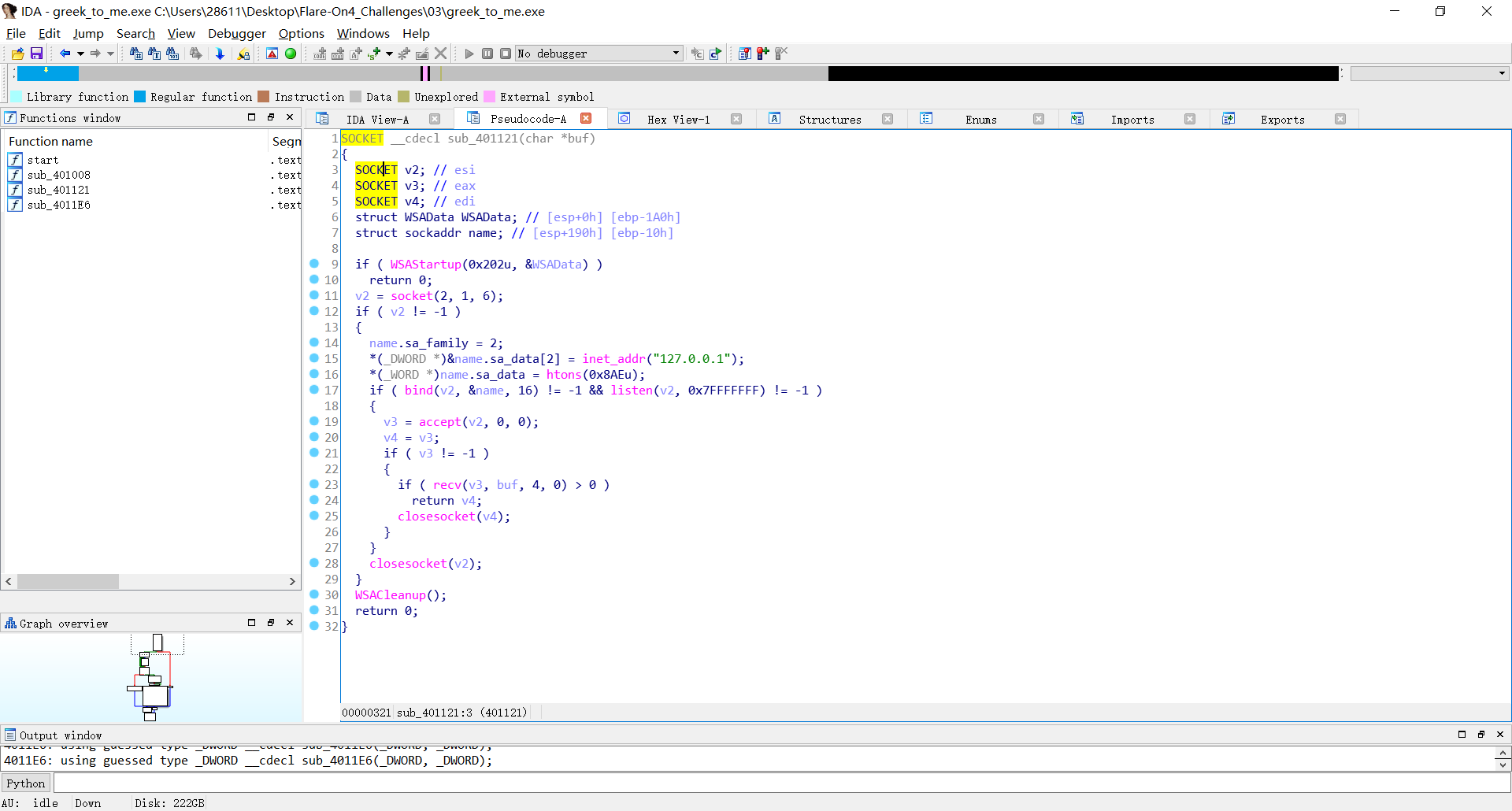
The WSAStartup function initiates use of the Winsock DLL by a process , The WSAStartup function initiates use of the Winsock DLL by a process , And we can see socket: SOCKET PASCAL FAR socket(int af,int type,int protocol)The parameter af USES it to identify the type of address , and then The bind function associates the socket with a local address , The listen function places a socket in a state in which it is listening for an incoming connection , The accept function permits an incoming connection attempt on a socket , The send function sends data on a connected socket , The recv function receives data from a connected or bound socket , The closesocket function closes an existing socket.
Htonl simply converts native byte order to network byte order : The so-called network byte order (big tail order) refers to a number is stored in memory "high to low, low to high
We know htons(0x8AEu)

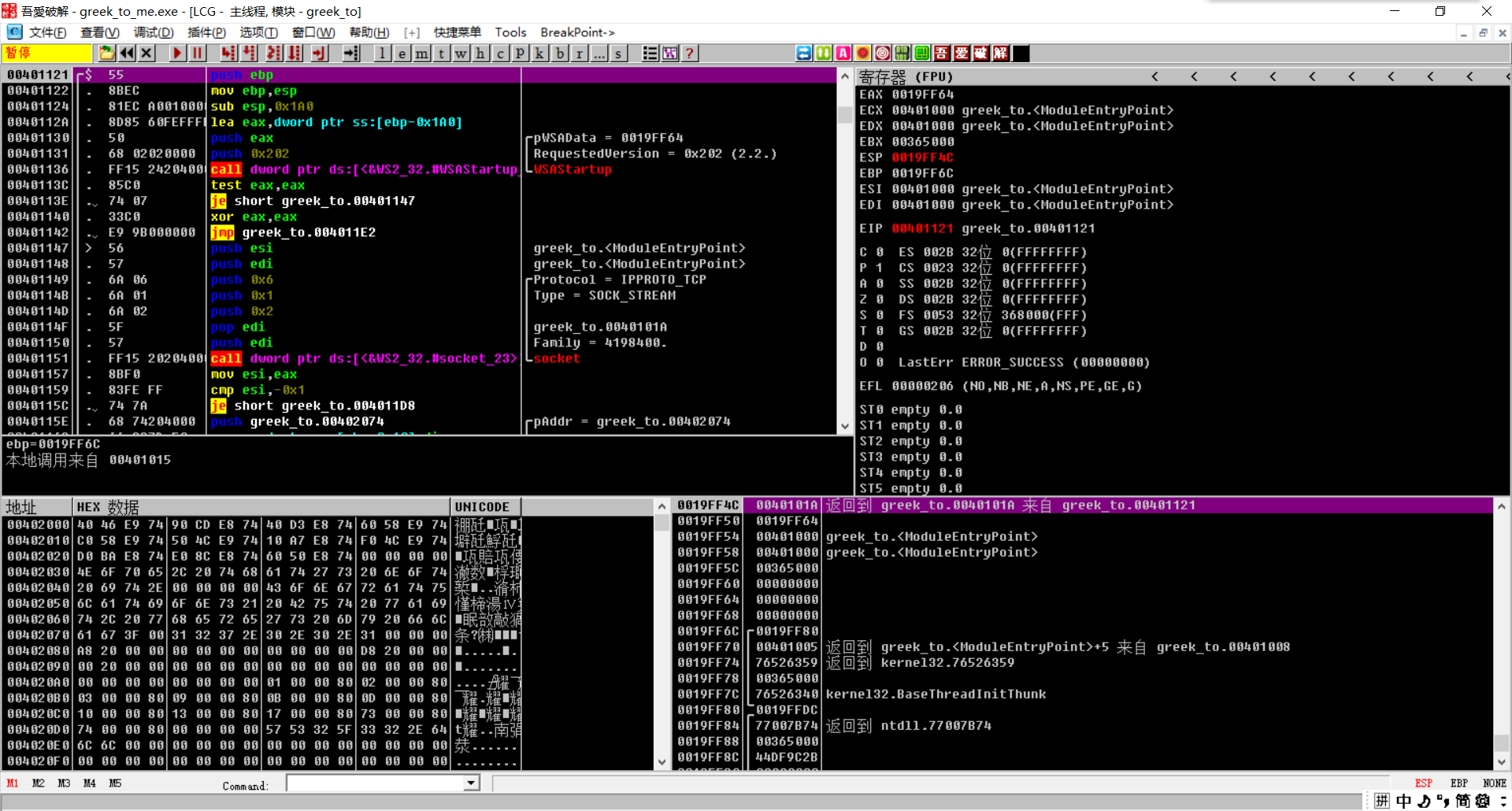
So here we are at the socket
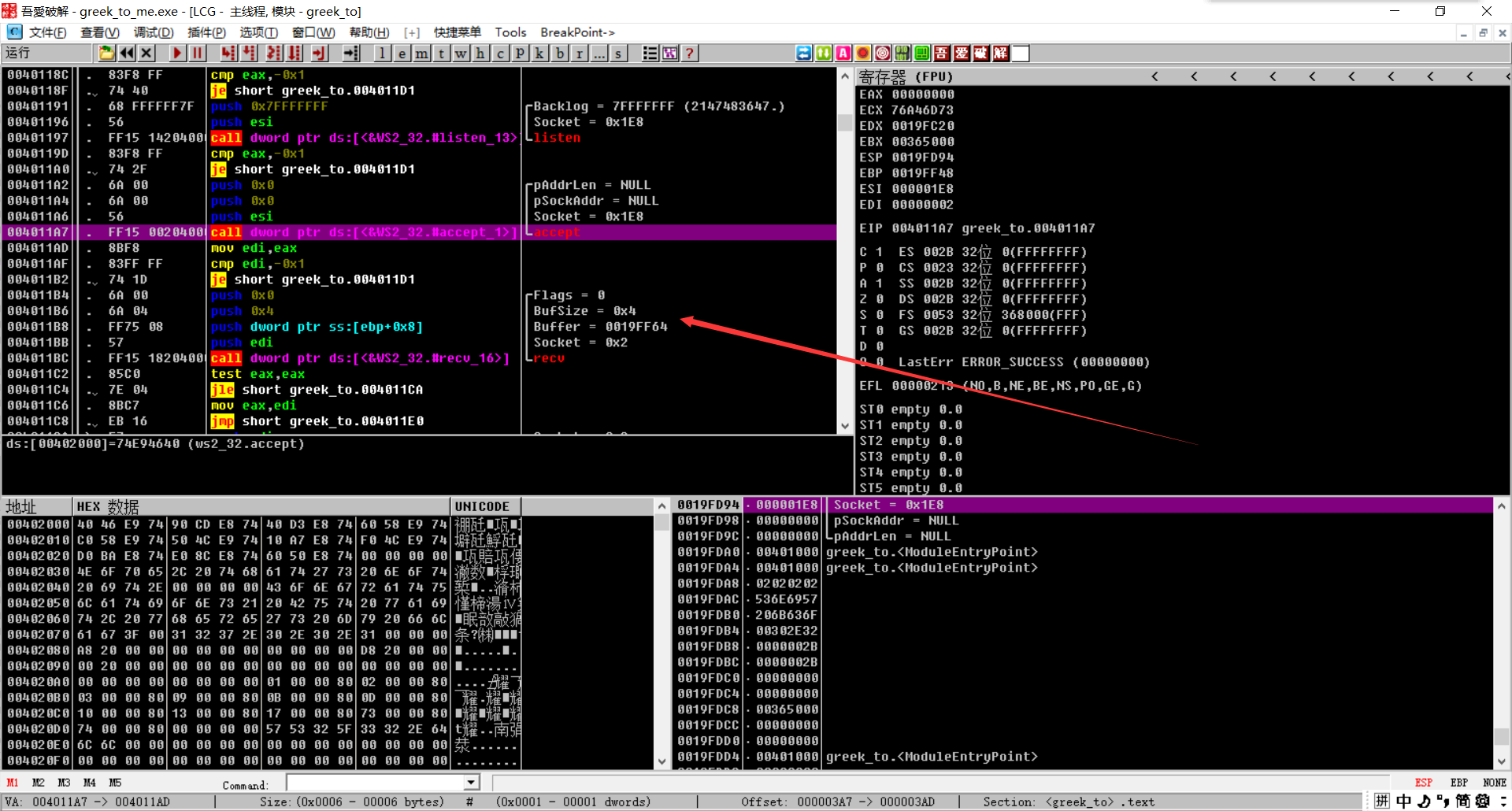
After finding the call, we need to call recv to read 4 bytes, which are in ebp+8 and will be closed immediately if we provide less than 4 bytes
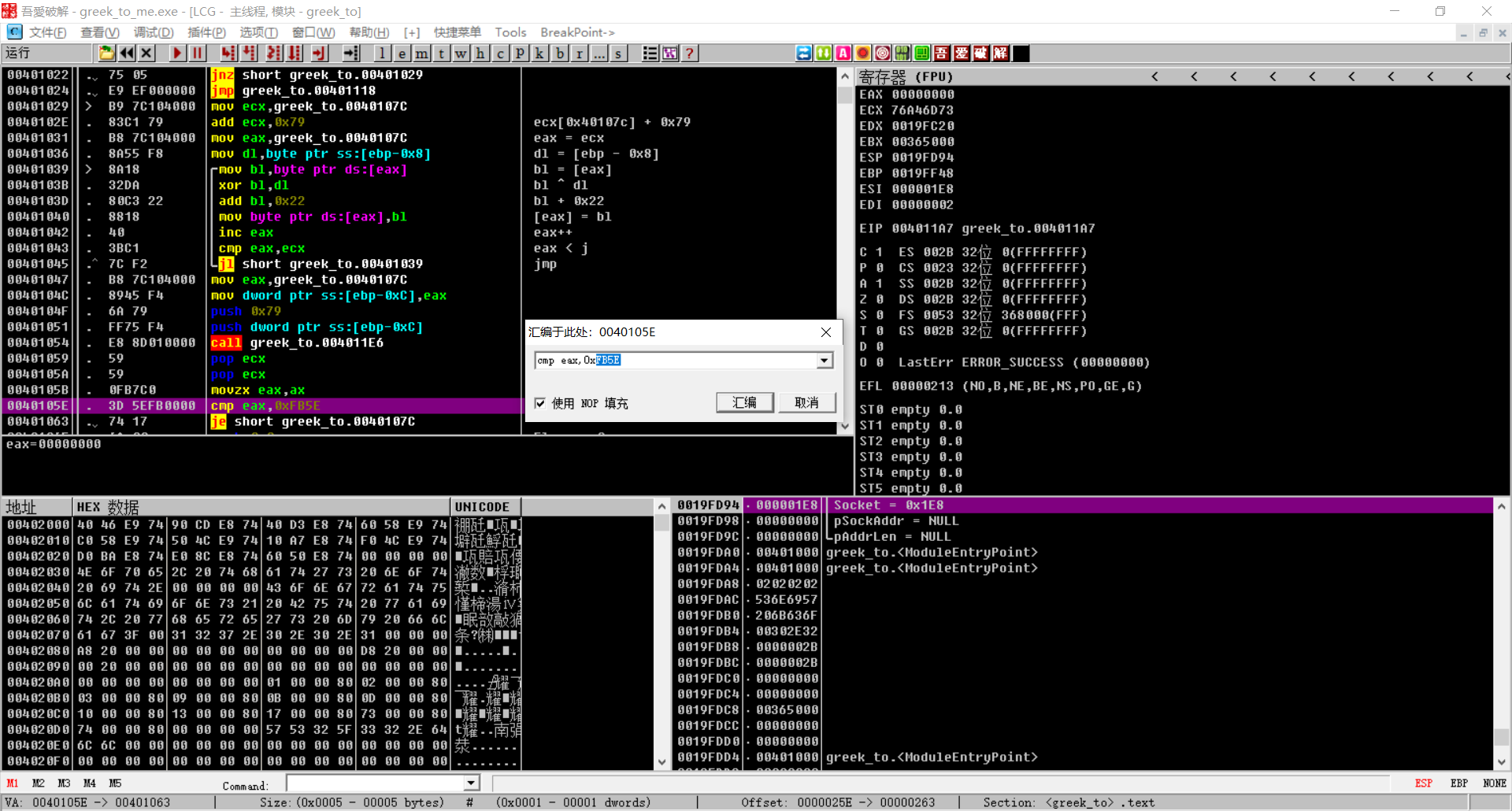
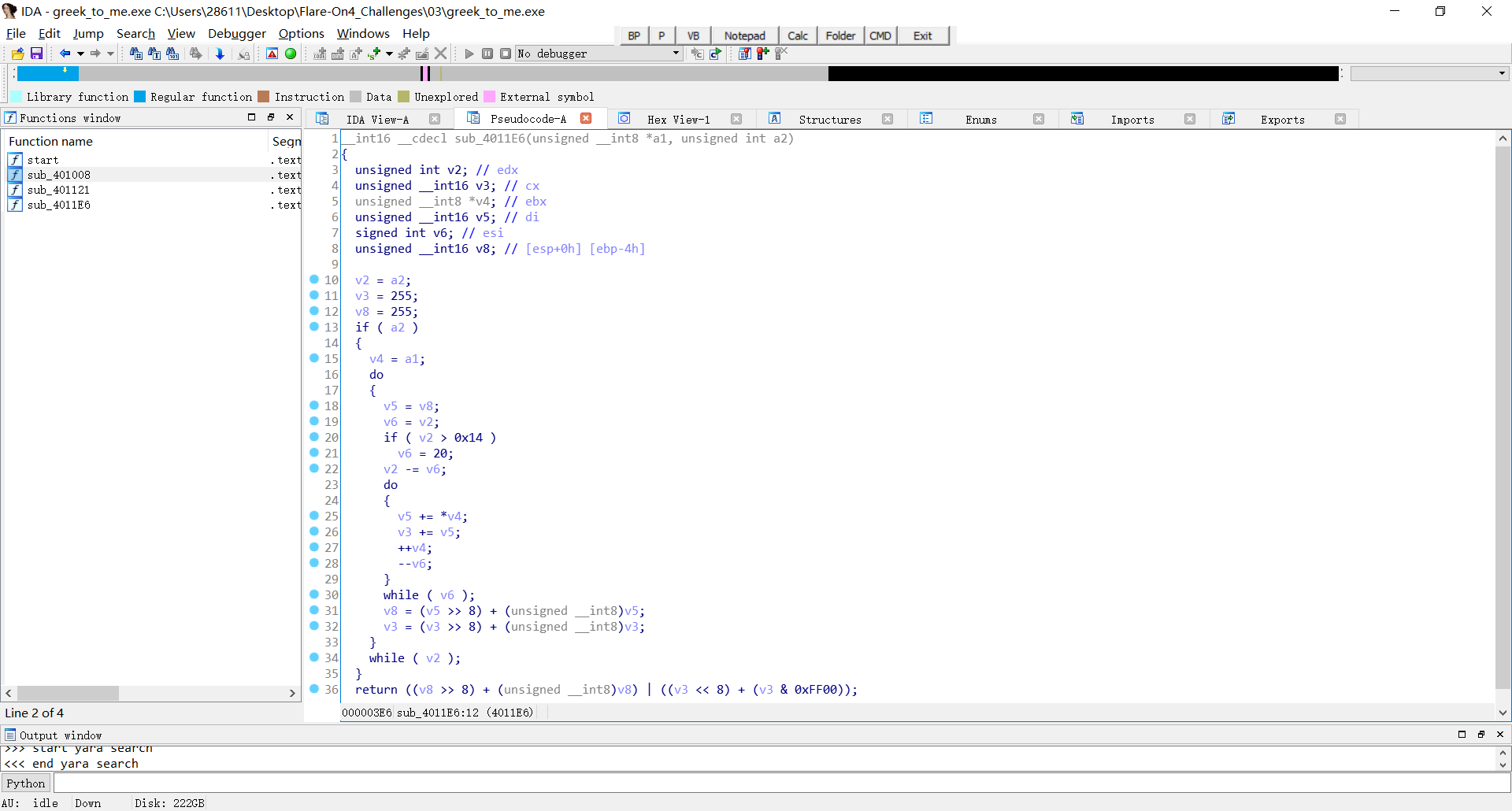
call 4011E6:this is Fletcher checksum
So we’re going to solve for the real key, and then we’re going to do xor, and then we’re going to compute the hash = 0xFB5E
Fletcher’s checksum
1 | uint16 Crc_CalculateISOChecksum(uint8 *pt_start_address, uint32 length) |
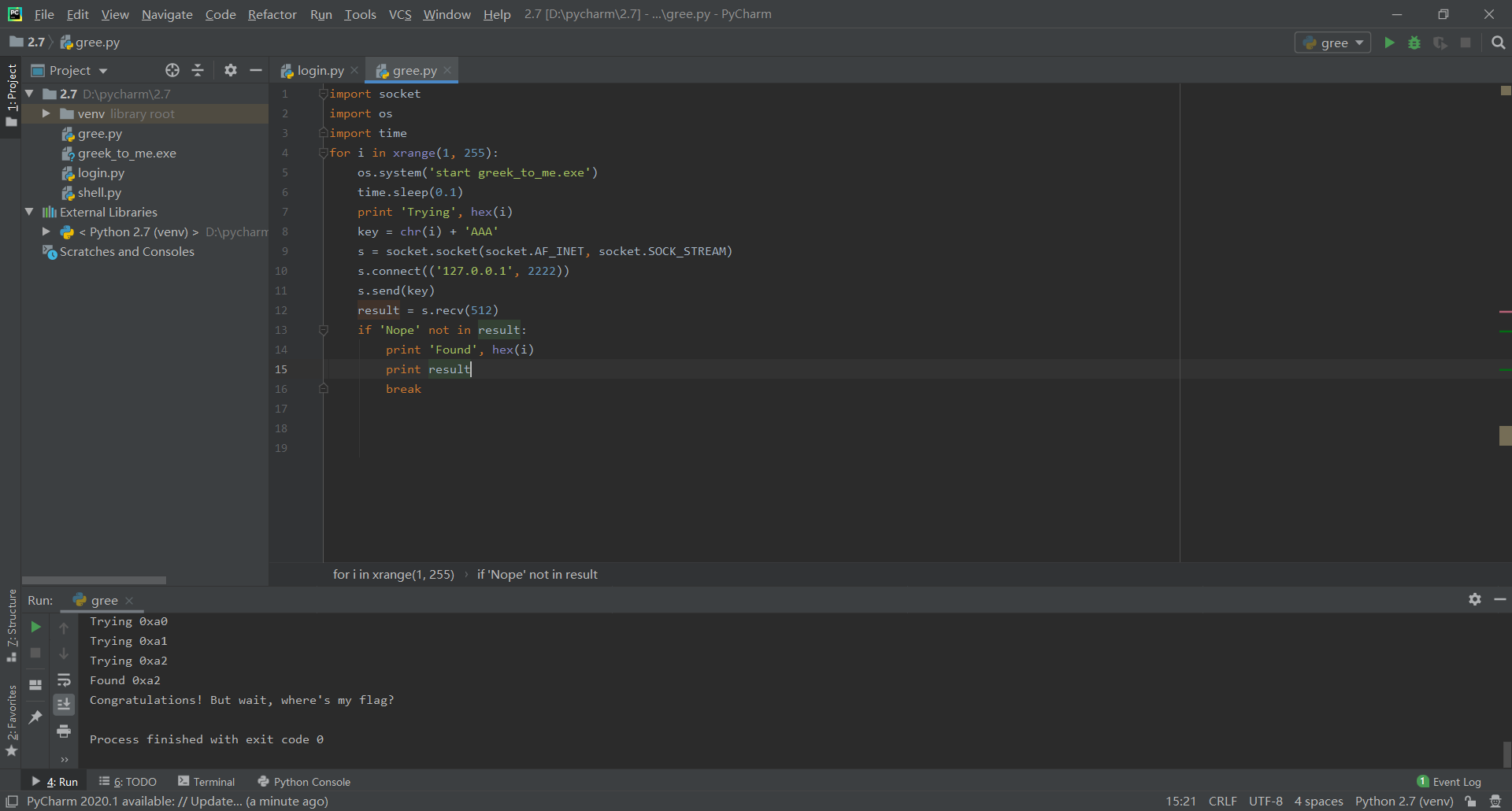
we fing key 0xA2
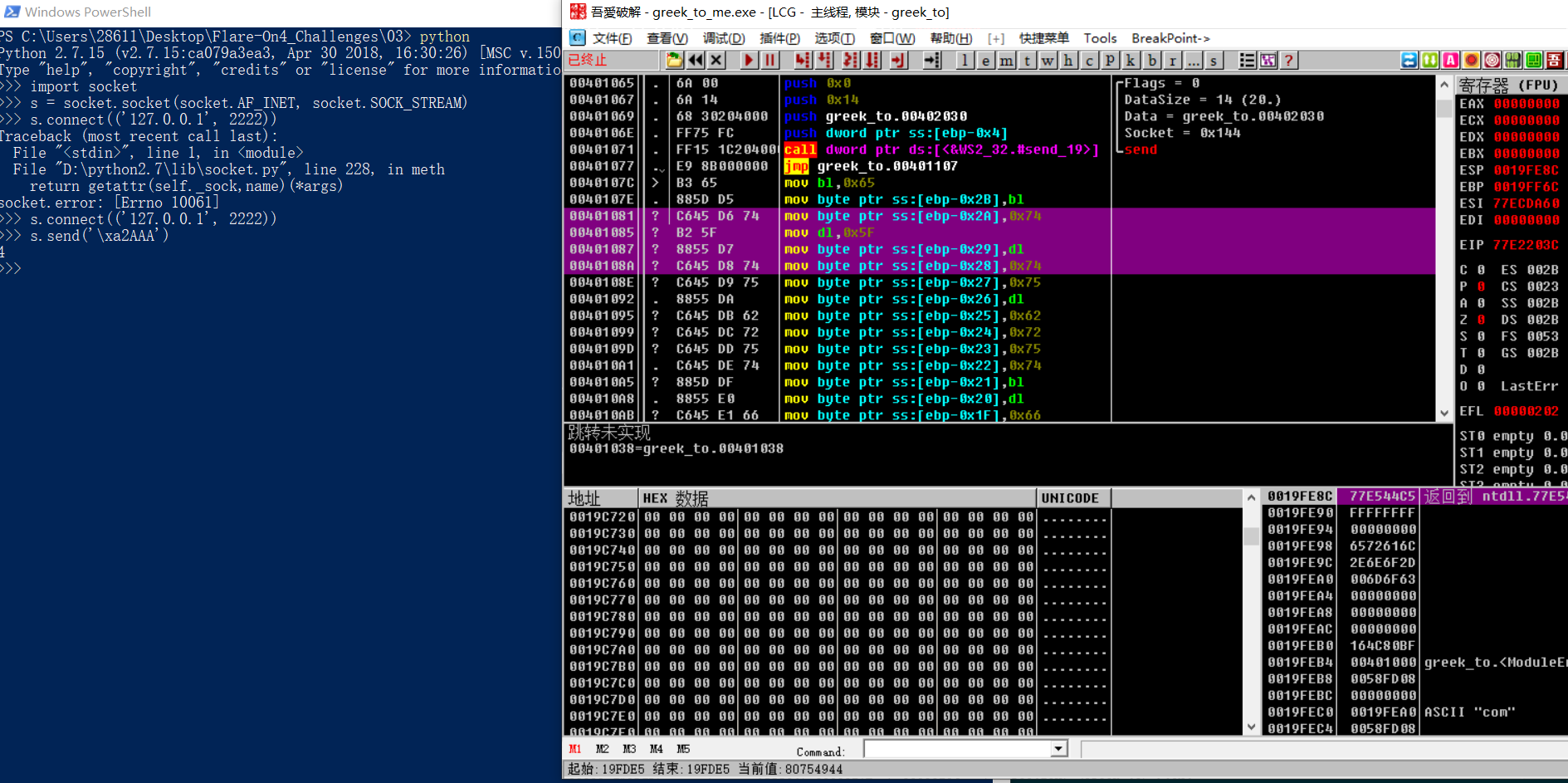
We find flag , Hit the break point to see
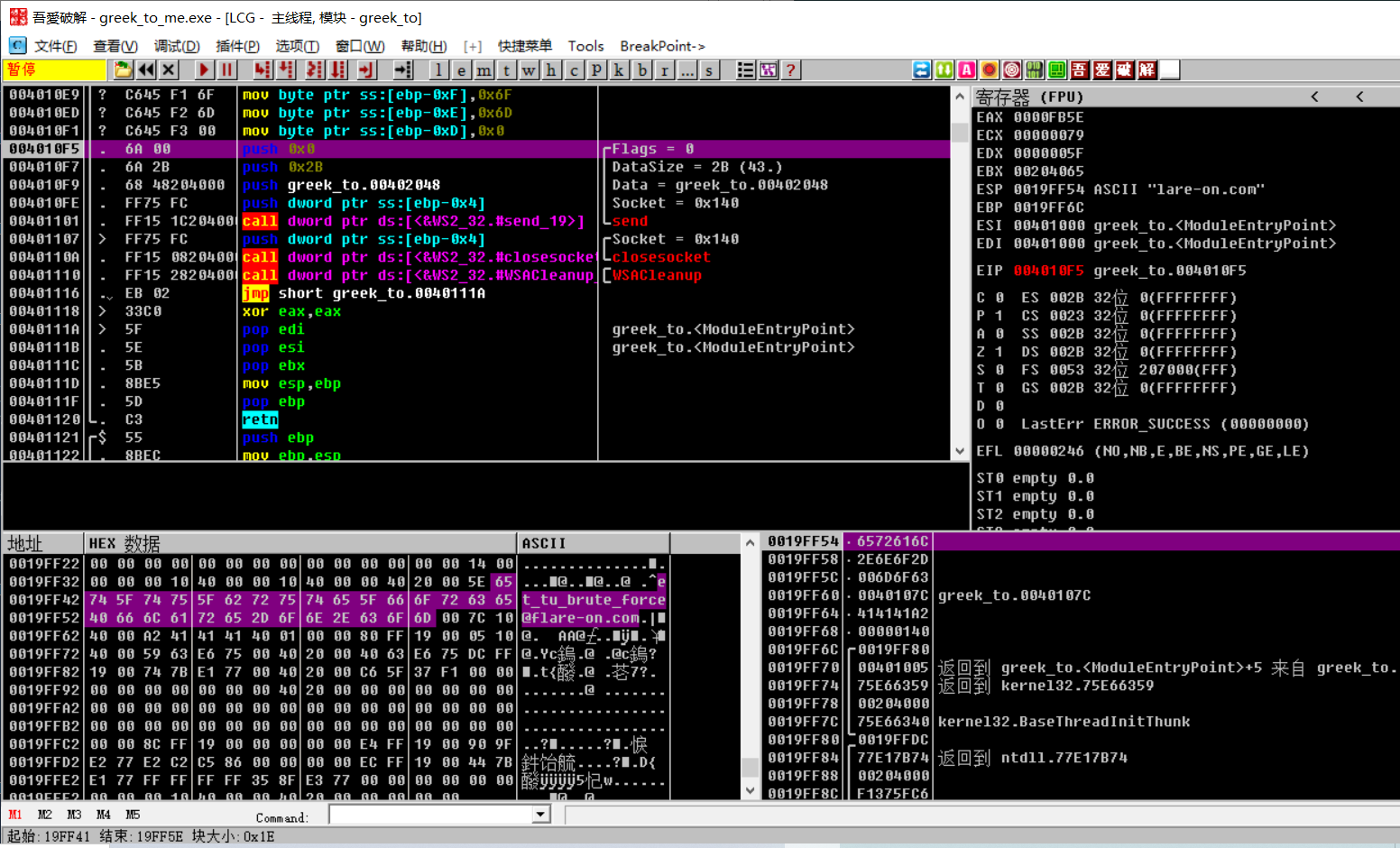
1 | //et_tu_brute_force@flare-on.com |
Challenge #4: notepad.exe
Open it and have a look
I can’t have some informations,but It’s nice to see notepad, which I talked about earlier in the book on the core principles of reverse engineering, when it was a PE structure
I put it in CFF and compared it to native notepad
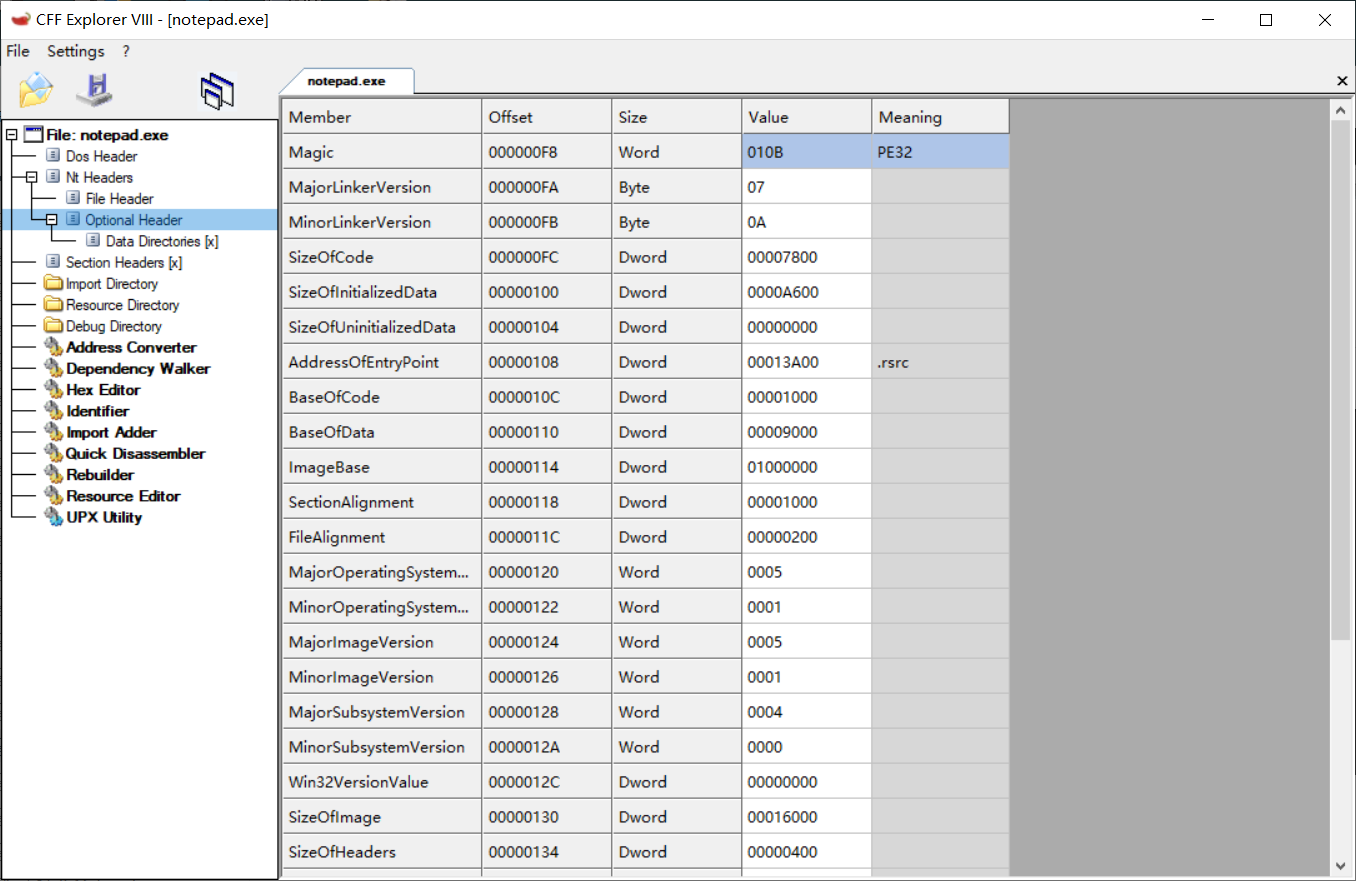
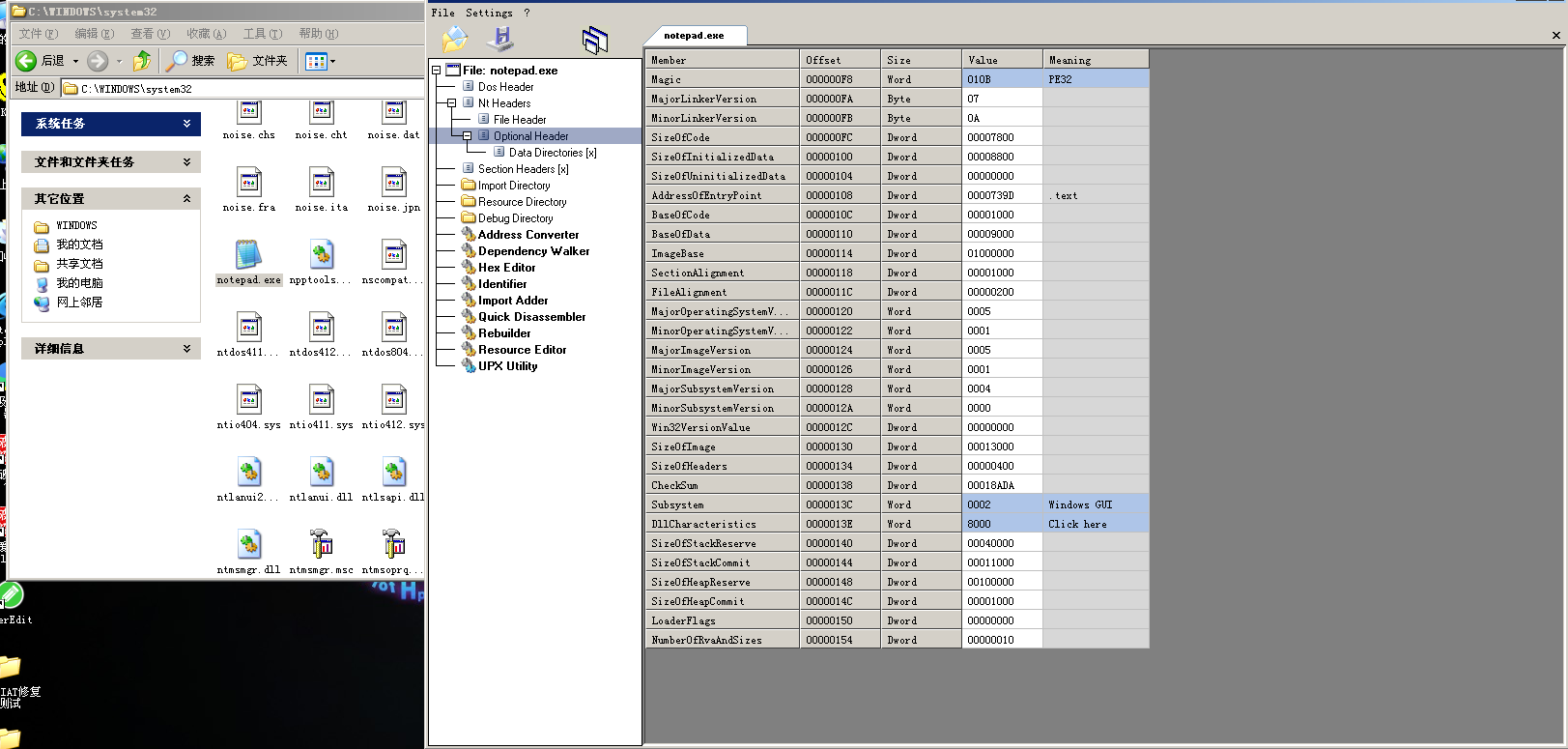
Offset: challenge ----- .rsrc my computer ---- .text
The.rsrc section contains the module’s resource information , Record a question that was asked during the interview:.data stores data, while.rdata sometimes stores IAT data in part and structures in part
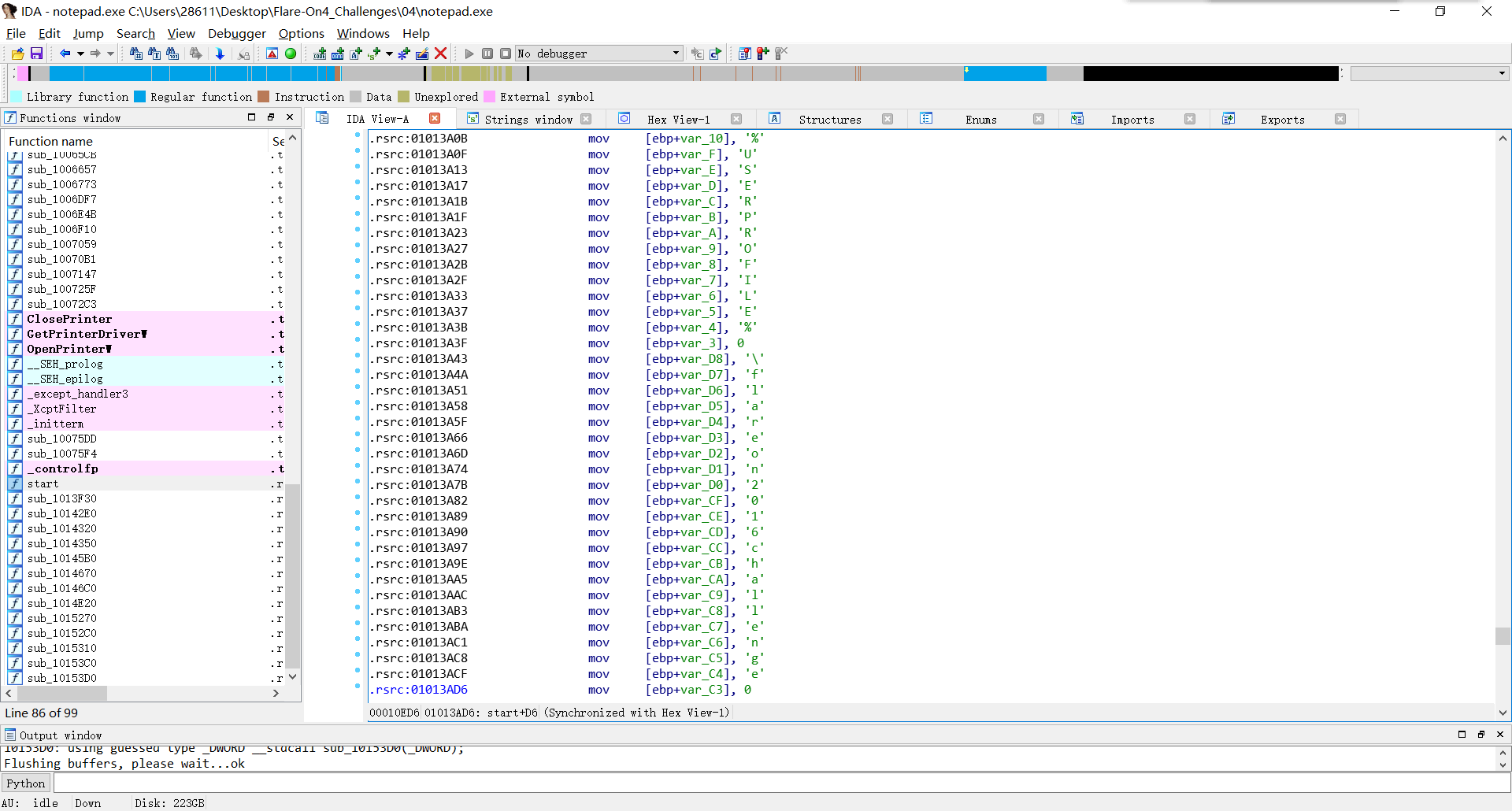
1 | %USERPROFILE%\flareon2016challenge |
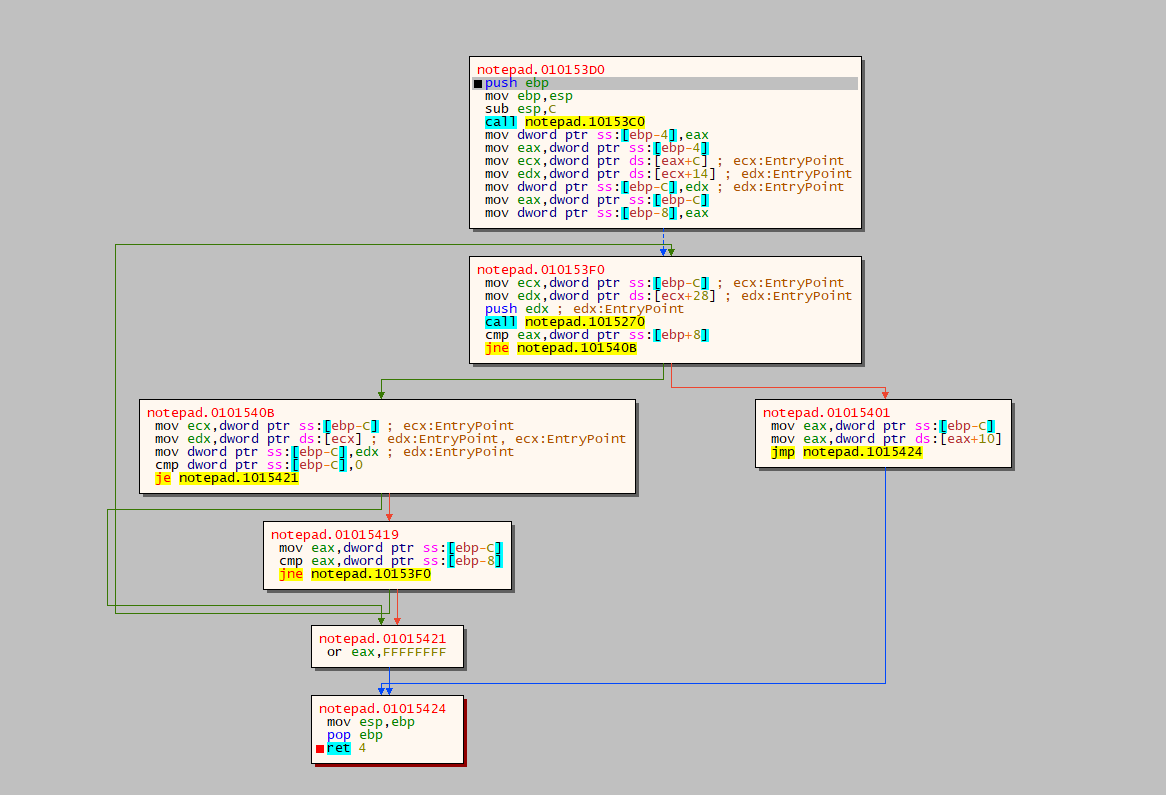
0x10153C0:
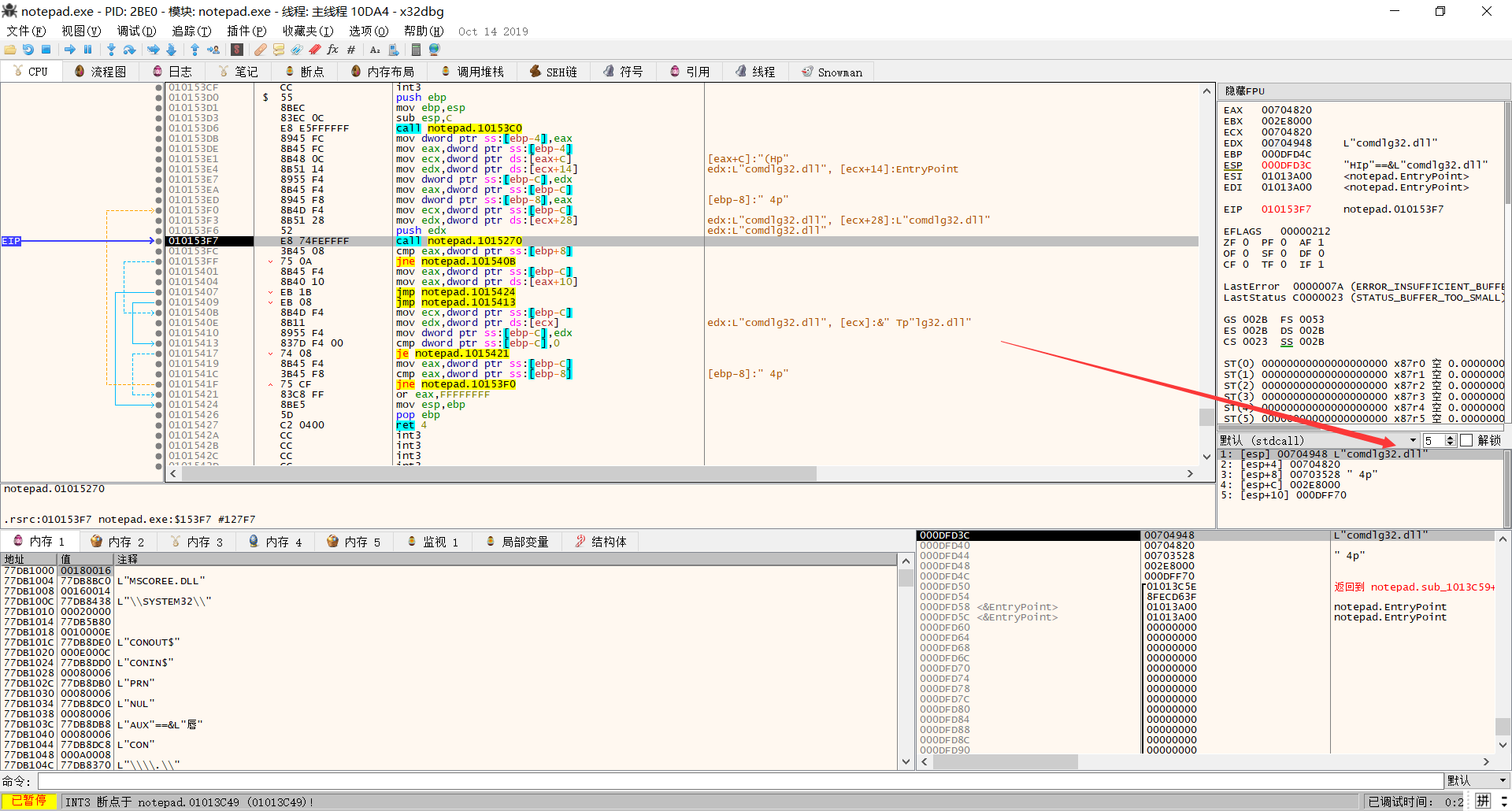
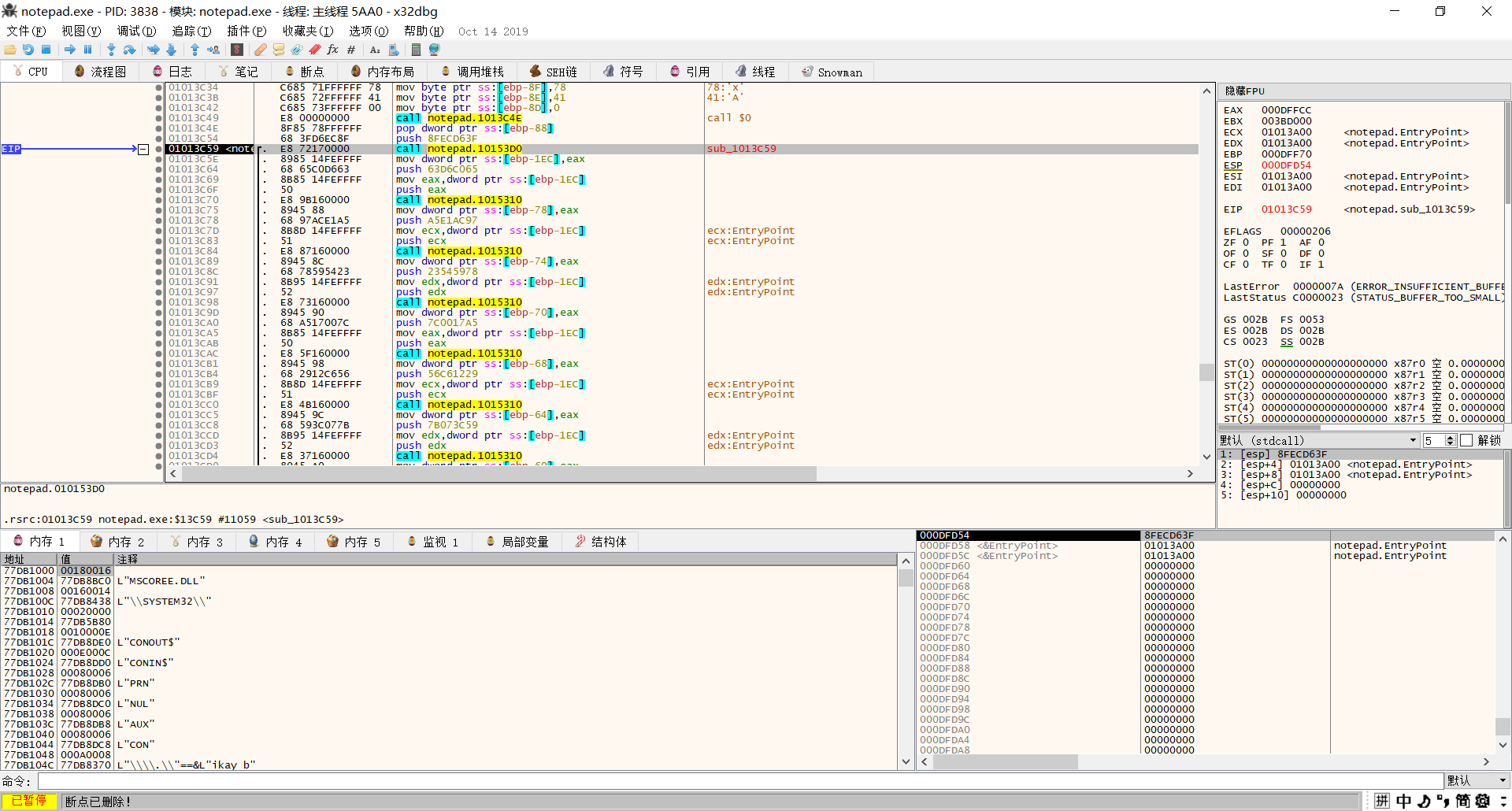
We can see lots of things , for example : 0x8FECD63F 0x63D6C065…